I am having difficulty configuring YaCy to participate in the greater pool. My ISP blocks all useful inbound ports, and for privacy reasons, I use a public VPN at the router level for outbound traffic to prevent them from tracking and selling my information. To work around this, I have set up Cloudflare Tunnel to route traffic inbound from my domain (protobit.io) to my services running in Hashicorp Nomad. This has been working well for everything else I’ve stood up thus far, but YaCy is not able to participate in the peer to peer pool. I’m pretty sure something in YaCy itself is missing some relevant configuration, but I cannot find the place to set it.
Here is the outbound network path:
YaCy -> Podman container -> Nomad bridge network -> Host network -> router -> VPN
Inbound path:
Cloudflare DNS -> Cloudflare Tunnel (in Nomad) -> router DNS -> Traefik (in Nomad) -> YaCy SSL port.
Theoretically, with YaCy peer traffic all going over HTTP(S), it should work as well as the other services with this config. I have done my best to configure YaCy to announce to the world my public DNS name and port/protocol, but it seems to have ignored some of this config.
Due to the forum preventing new users from doing helpful things like post multiple screenshots, configs, or even links; I have a public share with all that here: [yacy - Nextcloud]
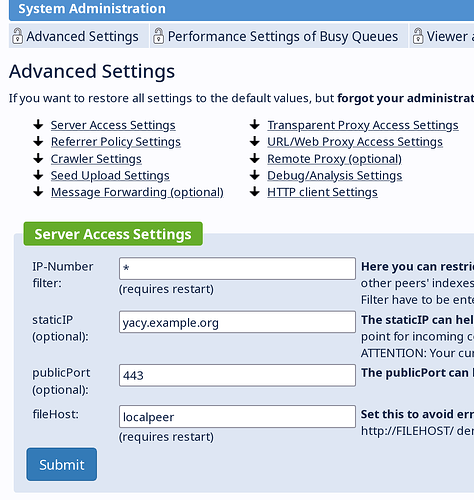
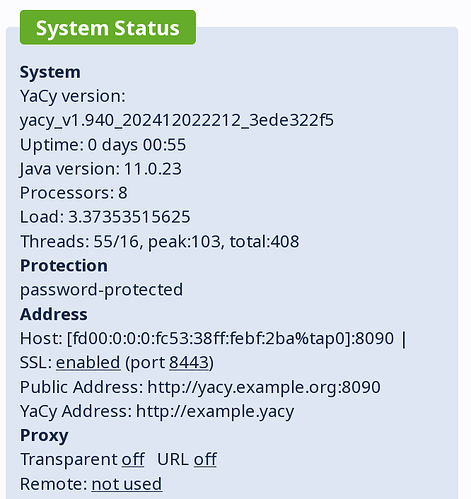
03 - Server Access Settings.png shows the only place I could find in the settings / docs where you can specify the public hostname and port. 02 - System Status.png makes it look as though the public hostname is only partially applied due to Host: []:80 and the Public Address not showing https:// or port 443. I tried to set the port to 443 on the Basic Configuration page, but pressing Save just resets it back to 80. I was not able to find anywhere else to set the hostname/address so that the field on the system status screen would show the public hostname.
The rest of my configs are in the share, and the instance is publicly reachable at https://yacy.protobit.io, so you can see that general connectivity via the tunnel is working.
The only thing I can think of that might be odd in this config is that I’m having Cloudflare Tunnel force all clients to come in via HTTPS, which then is plain HTTP to Traefik within my network. However, I have Traefik connecting to YaCy’s HTTPS port, ignoring the self-signed cert, in an effort to make the application believe that all traffic is HTTPS. Using HTTPS between cloudflared and Traefik would be problematic, as there would not be a way for me to get valid certs without considerable expense or pain with LetsEncrypt. Apart from this, I don’t really see how this is significantly different from having YaCy behind any other reverse proxy where the outside ports and hostname don’t match internal, which I believe is a supported config.
I’m hoping that there’s some config I’ve overlooked to announce to the other instances that they can reach mine via the tunnel with the public DNS over HTTPS, but I’m at a complete loss as to where that might be. None of the entries in System Administration -> Advanced Config seemed to apply beyond what I’ve already done. Would any of the fine folks in here be willing to lend a hand in helping get the config fixed?