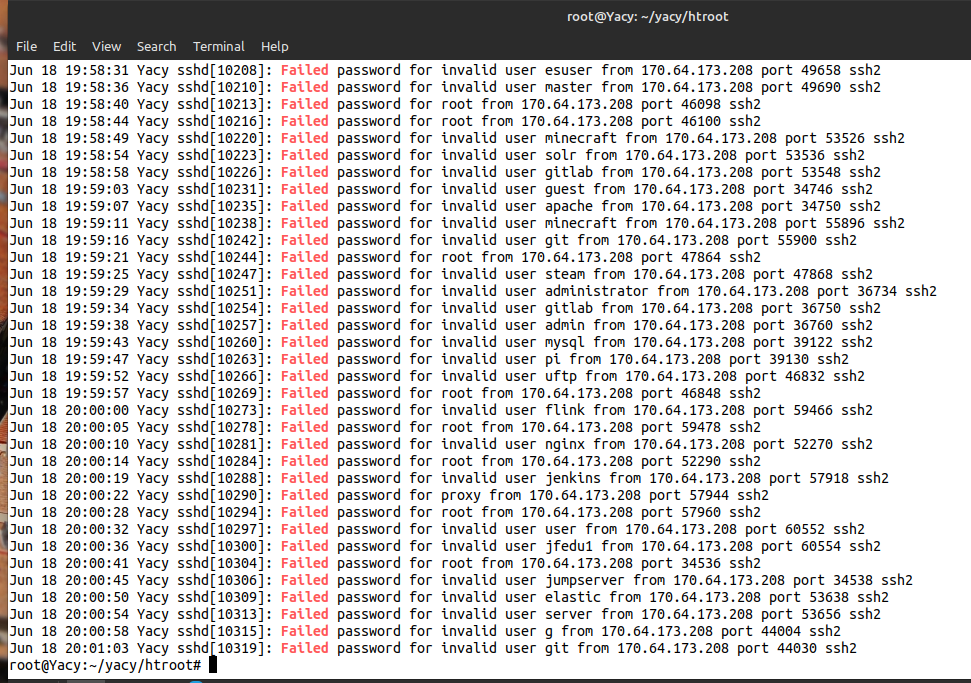
A couple IP addresses have been repeatedly trying to login to a Yacy server.
- 8.150.8.211 (China?)
- 170.64.173.208 (USA?)
Those addresses are now blocked in iptables.
If you are running a Linux server, you could see failed login attempts with a command like this:
grep -i failed /var/log/auth.log
Thank you for pointing out that issue. In linux there are tools like Fail2ban which automatically block such clients. While I cant remember that we had strong issues in YaCy with scripted attacks we still maybe should increase protection.
1 Like
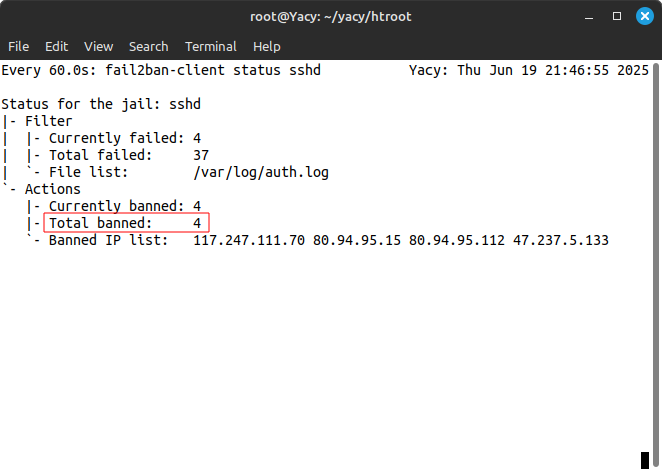
Thanks for the tip! I also installed fail2ban and in less than an hour of running, it’s already caught some bad actors and put them in jail. It does seem like a good idea… for the server to automatically ban those IP addresses that sent failed logins repeatedly… so we don’t have to watch the logs.